Evgeni Golov: show your desk

Some days ago I posted a picture of my desk on Mastodon and Twitter.
 After that I got multiple questions about the setup, so I thought "Michael and Michael did posts about their setups, you could too!"
And well, here we are ;-)
desk
The desk is a Flexispot E5B frame with a 200 80 2.6cm oak table top.
The Flexispot E5 (the B stands for black) is a rather cheap (as in not expensive) standing desk frame. It has a retail price of 379 , but you can often get it as low as 299 on sale.
Add a nice table top from a local store (mine was like 99 ), a bit of wood oil and work and you get a nice standing desk for less than 500 .
The frame has three memory positions, but I only use two: one for sitting, one for standing, and a "change position" timer that I never used so far.
The table top has a bit of a swing when in standing position (mine is at 104cm according to the electronics in the table), but not enough to disturb typing on the keyboard or thinking. I certainly wouldn't place a sewing machine up there, but that was not a requirement anyways ;)
To compare: the IKEA Bekant table has a similar, maybe even slightly stronger swing.
chair
Speaking of IKEA The chair is an IKEA Volmar. They don't seem to sell it since mid 2019 anymore though, so no link here.
hardware
laptop
A Lenovo ThinkPad T480s, i7-8650U, 24GB RAM, running Fedora 32 Workstation. Just enough power while not too big and heavy. Full of stickers, because I stickers!
It's connected to a Lenovo ThinkPad Thunderbolt 3 Dock (Gen 1). After 2 years with that thing, I'm still not sure what to think about it, as I had various issues with it over the time:
After that I got multiple questions about the setup, so I thought "Michael and Michael did posts about their setups, you could too!"
And well, here we are ;-)
desk
The desk is a Flexispot E5B frame with a 200 80 2.6cm oak table top.
The Flexispot E5 (the B stands for black) is a rather cheap (as in not expensive) standing desk frame. It has a retail price of 379 , but you can often get it as low as 299 on sale.
Add a nice table top from a local store (mine was like 99 ), a bit of wood oil and work and you get a nice standing desk for less than 500 .
The frame has three memory positions, but I only use two: one for sitting, one for standing, and a "change position" timer that I never used so far.
The table top has a bit of a swing when in standing position (mine is at 104cm according to the electronics in the table), but not enough to disturb typing on the keyboard or thinking. I certainly wouldn't place a sewing machine up there, but that was not a requirement anyways ;)
To compare: the IKEA Bekant table has a similar, maybe even slightly stronger swing.
chair
Speaking of IKEA The chair is an IKEA Volmar. They don't seem to sell it since mid 2019 anymore though, so no link here.
hardware
laptop
A Lenovo ThinkPad T480s, i7-8650U, 24GB RAM, running Fedora 32 Workstation. Just enough power while not too big and heavy. Full of stickers, because I stickers!
It's connected to a Lenovo ThinkPad Thunderbolt 3 Dock (Gen 1). After 2 years with that thing, I'm still not sure what to think about it, as I had various issues with it over the time:
 After that I got multiple questions about the setup, so I thought "Michael and Michael did posts about their setups, you could too!"
And well, here we are ;-)
desk
The desk is a Flexispot E5B frame with a 200 80 2.6cm oak table top.
The Flexispot E5 (the B stands for black) is a rather cheap (as in not expensive) standing desk frame. It has a retail price of 379 , but you can often get it as low as 299 on sale.
Add a nice table top from a local store (mine was like 99 ), a bit of wood oil and work and you get a nice standing desk for less than 500 .
The frame has three memory positions, but I only use two: one for sitting, one for standing, and a "change position" timer that I never used so far.
The table top has a bit of a swing when in standing position (mine is at 104cm according to the electronics in the table), but not enough to disturb typing on the keyboard or thinking. I certainly wouldn't place a sewing machine up there, but that was not a requirement anyways ;)
To compare: the IKEA Bekant table has a similar, maybe even slightly stronger swing.
chair
Speaking of IKEA The chair is an IKEA Volmar. They don't seem to sell it since mid 2019 anymore though, so no link here.
hardware
laptop
A Lenovo ThinkPad T480s, i7-8650U, 24GB RAM, running Fedora 32 Workstation. Just enough power while not too big and heavy. Full of stickers, because I stickers!
It's connected to a Lenovo ThinkPad Thunderbolt 3 Dock (Gen 1). After 2 years with that thing, I'm still not sure what to think about it, as I had various issues with it over the time:
After that I got multiple questions about the setup, so I thought "Michael and Michael did posts about their setups, you could too!"
And well, here we are ;-)
desk
The desk is a Flexispot E5B frame with a 200 80 2.6cm oak table top.
The Flexispot E5 (the B stands for black) is a rather cheap (as in not expensive) standing desk frame. It has a retail price of 379 , but you can often get it as low as 299 on sale.
Add a nice table top from a local store (mine was like 99 ), a bit of wood oil and work and you get a nice standing desk for less than 500 .
The frame has three memory positions, but I only use two: one for sitting, one for standing, and a "change position" timer that I never used so far.
The table top has a bit of a swing when in standing position (mine is at 104cm according to the electronics in the table), but not enough to disturb typing on the keyboard or thinking. I certainly wouldn't place a sewing machine up there, but that was not a requirement anyways ;)
To compare: the IKEA Bekant table has a similar, maybe even slightly stronger swing.
chair
Speaking of IKEA The chair is an IKEA Volmar. They don't seem to sell it since mid 2019 anymore though, so no link here.
hardware
laptop
A Lenovo ThinkPad T480s, i7-8650U, 24GB RAM, running Fedora 32 Workstation. Just enough power while not too big and heavy. Full of stickers, because I stickers!
It's connected to a Lenovo ThinkPad Thunderbolt 3 Dock (Gen 1). After 2 years with that thing, I'm still not sure what to think about it, as I had various issues with it over the time:
- the internal USB hub just vanishing from existence until a full power cycle of the dock was performed, but that might have been caused by my USB-switch which I recently removed.
- the NIC negotiating at 100MBit/s instead of 1000MBit/s and then keeping on re-negotiating every few minutes, disconnecting me from the network, but I've not seen that since the Fedora 32 upgrade.
- the USB-attached keyboard not working during boot as it needs some Thunderbolt magic.
 Float/String Conversion in Picolibc: Enter Ry
I
Float/String Conversion in Picolibc: Enter Ry
I 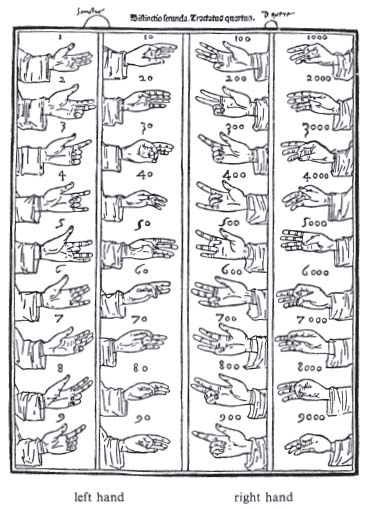 (Note that in this diagram 60 is, in fact, wrong,
and this picture swaps the hundreds and the thousands.)
We ll start with the units.
The last three fingers of the left hand, middle, ring, and pinkie,
are used to form them.
Zero is formed with an open hand, the opposite of the finger
counting we re used to.
One is formed by bending the middle joint of the pinkie,
two by including the ring finger and three by including the
middle finger, all at the middle joint.
You ll want to keep all these bends fairly loose, as otherwise
these numbers can get quite uncomfortable.
For four, you extend your pinkie again, for five, also raise your
ring finger, and for six, you raise your middle finger as well, but
then lower your ring finger.
For seven you bend your pinkie at the bottom joint, for eight
adding your ring finger, and for nine, including your middle
finger. This mirrors what you did for one, two and three, but
bending the finger at the bottom joint now instead.
This leaves your thumb and index finger for the tens.
For ten, touch the nail of your index finger to the inside of your top thumb
joint.
For twenty, put your thumb between your index and middle fingers.
For thirty, touch the nails of your thumb and index fingers.
For forty, bend your index finger slightly towards your palm
and place your thumb between the middle and top knuckle of your
index finger.
For fifty, place your thumb against your palm.
For sixty, leave your thumb where it is and wrap your index
finger around it (the diagram above is wrong).
For seventy, move your thumb so that the nail touches between the
middle and top knuckle of your index finger.
For eighty, flip your thumb so that the bottom of it now
touches the spot between the middle and top knuckle of your index
finger.
For ninety, touch the nail of your index finger to your bottom
thumb joint.
The hundreds and thousands use the same positions on the right
hand, with the units being the thousands and the tens being the
hundreds. One account, from which the picture above comes, swaps
these two, but the first account we have uses this ordering.
Combining all these symbols, you can count all the way to 9,999
yourself on just two hands. Try it!
(Note that in this diagram 60 is, in fact, wrong,
and this picture swaps the hundreds and the thousands.)
We ll start with the units.
The last three fingers of the left hand, middle, ring, and pinkie,
are used to form them.
Zero is formed with an open hand, the opposite of the finger
counting we re used to.
One is formed by bending the middle joint of the pinkie,
two by including the ring finger and three by including the
middle finger, all at the middle joint.
You ll want to keep all these bends fairly loose, as otherwise
these numbers can get quite uncomfortable.
For four, you extend your pinkie again, for five, also raise your
ring finger, and for six, you raise your middle finger as well, but
then lower your ring finger.
For seven you bend your pinkie at the bottom joint, for eight
adding your ring finger, and for nine, including your middle
finger. This mirrors what you did for one, two and three, but
bending the finger at the bottom joint now instead.
This leaves your thumb and index finger for the tens.
For ten, touch the nail of your index finger to the inside of your top thumb
joint.
For twenty, put your thumb between your index and middle fingers.
For thirty, touch the nails of your thumb and index fingers.
For forty, bend your index finger slightly towards your palm
and place your thumb between the middle and top knuckle of your
index finger.
For fifty, place your thumb against your palm.
For sixty, leave your thumb where it is and wrap your index
finger around it (the diagram above is wrong).
For seventy, move your thumb so that the nail touches between the
middle and top knuckle of your index finger.
For eighty, flip your thumb so that the bottom of it now
touches the spot between the middle and top knuckle of your index
finger.
For ninety, touch the nail of your index finger to your bottom
thumb joint.
The hundreds and thousands use the same positions on the right
hand, with the units being the thousands and the tens being the
hundreds. One account, from which the picture above comes, swaps
these two, but the first account we have uses this ordering.
Combining all these symbols, you can count all the way to 9,999
yourself on just two hands. Try it!







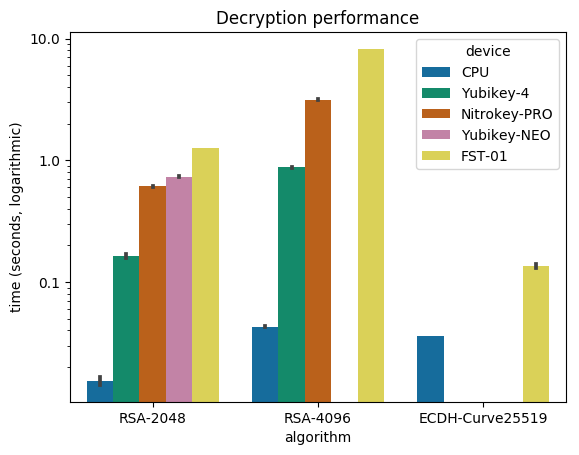
 Debian
devscripts
Before deciding to take an
Debian
devscripts
Before deciding to take an 
 A new version 0.2.0 of the
A new version 0.2.0 of the  The
The